BEST Agamotto
Cloud SIEM Management Solution
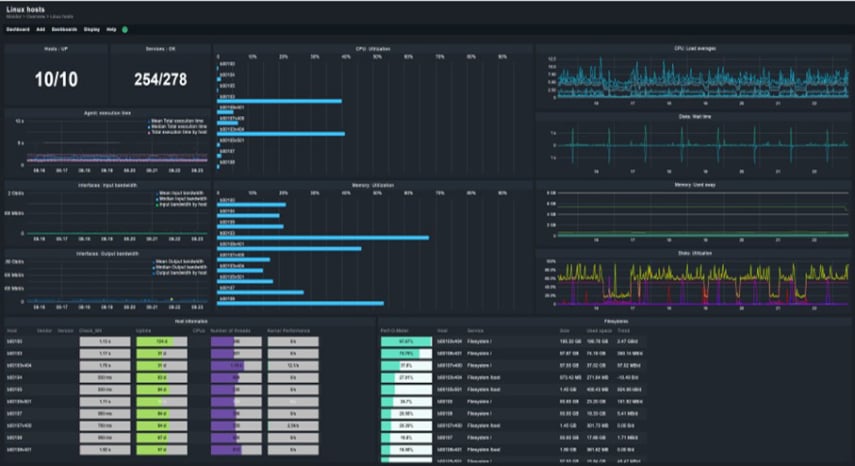
Agamotto provides cover for your public clouds, private clouds, and on-premises data centers.
Endpoint Security
•Configuration Assessment
•Extended Detection and Response
•File Integrity Monitoring
Threat Intelligence
•Threat Hunting
•IT Hygiene
•Vulnerability Detection
Security Operations
•Log Data Analysis
•Malware Detection
•Audit and Compliance